Aruba Clearpass syslog User-ID with Palo Alto
Aruba's Clearpass Policy Manager (CPPM) and Palo Alto's (PAN) Next Generation Firewall (NGFW) have a very capable User-ID integration via native APIs. However, I ran into a unique situation where my customer's NGFW could not handle the amount of requests that were coming in from CPPM. I haven't found documentation, but I believe that PAN has initiated a rate limit on their API calls in later firmware versions. While I understand why you would want to rate limit API calls; user connections are what they are. If they connect we need to pass that information up. USER-ID API calls were so rapid CPPM was falling on its face trying to keep up. The underlying reason seemed to be that that CPPM would send a request and wait for a period of time for an answer. The problem resided in the fact that the NGFW took a long time to fail. Which meant CPPM processing time exponentially got out of hand. Eventually, CPPM would just fall on its face. So, I had to find an alternative way.
If you have ever had exposure to either CPPM or a PAN NGFW you know how extremely flexible they are. I knew that there had to be an alternate way of getting this data into the firewall. Insert syslog.
What is syslog
If you're unaware of syslog, it's a technology as old as computers. That statement is 60% true, 100% of the time. The idea is that a system can send standard formatted logs to a centralized system where it can be processed. The trouble with that is: everyone went rogue. There are many formats, and you have to be a cryptography expert to decipher them. I am almost kidding, but there are many systems that agree on Common Event Format (CEF). We're lucky here in that PAN and Aruba agree we should use CEF. Syslog uses port 514 UDP by default. So by the nature of the IP protocol, it is best effort (BE).
What is USER-ID
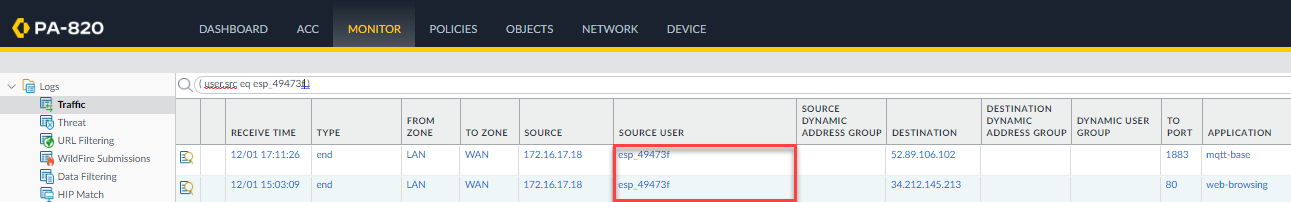
User-ID is the process of a PAN NGFW gathering user identity from an external identity provider (IdP) or other source. This is very important for a multitude of reasons. You may want to apply security policies based on an user's Active Directory group membership or a plethora of other attributes tied to users.
PreReqs
So, a few things need to happen for the firewall to process the syslog messages.
1. We need to add the fields we want to the logs before we send them.
2. Send the logs to the firewall.
3. Explicitly accept the logs.
4. Configure the firewall to process the incoming logs and their fields.
Clearpass Configuration
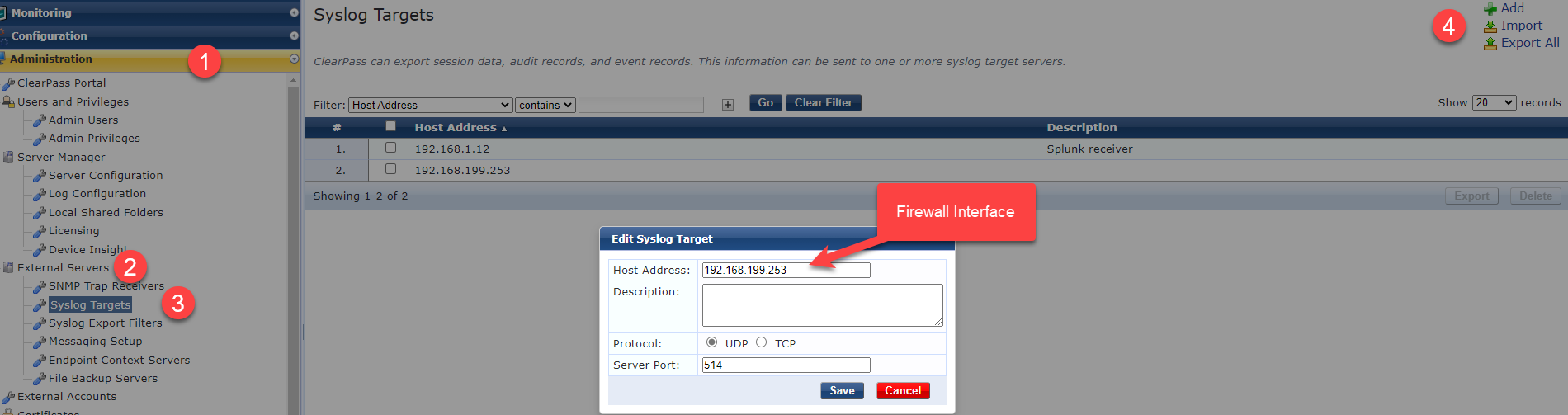
1. Configure a syslog target.
2. Configure syslog export filters.
In step 5 below select the appropriate syslog target that you configured in step 1.
The facility level generally means the log level. 0-7 means least informative to most informative. Admittedly, I haven't looked at the different levels to see if you could get the same data at a lower level. Ideally, you would you use the least level log level so CPPM isn't hammering the firewall. This is a lab, so I'm setting it to 7.
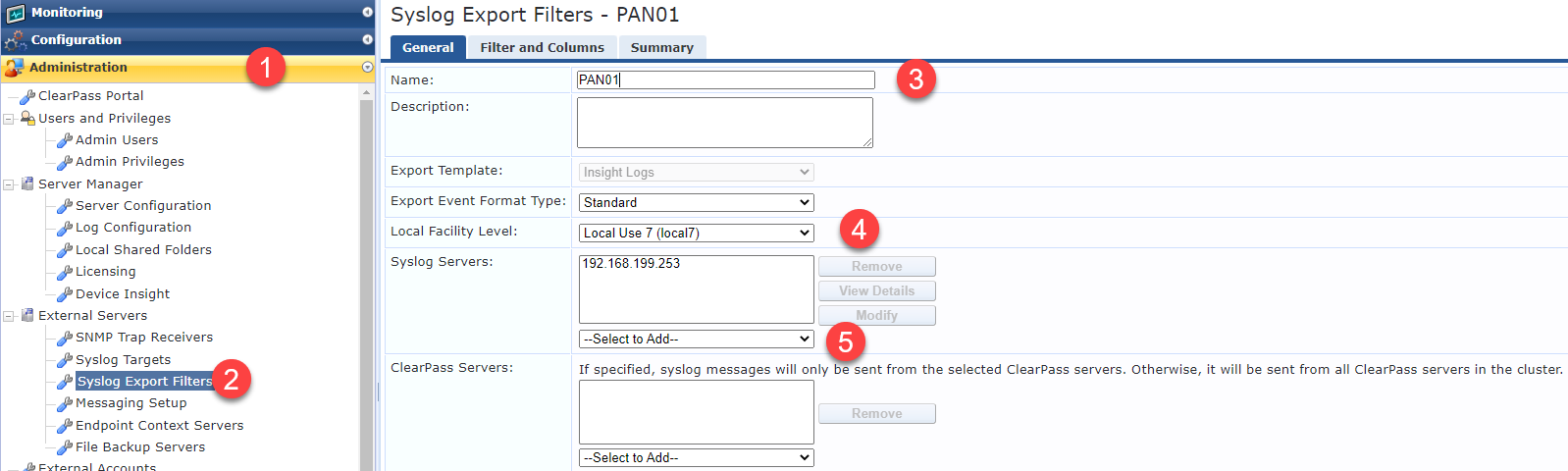
3. Configure syslog Export Filter columns.
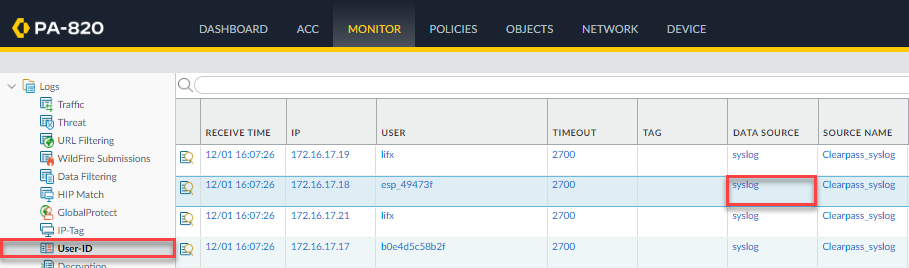
For our purposes, it only cares about the username to IP mapping. So this step is quite straight forward. Theoretically, you could also pass up roles via syslog, but I haven't tested it enough to put it here.
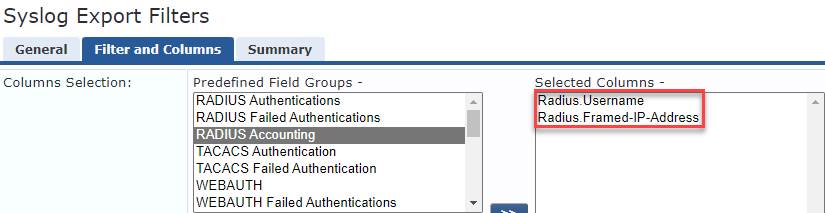
Predefined Field Groups -> Select Radius Accounting. Any predefined fields deleted except for Radius.Username and Radius.Framed-IP-Address (Client's IP Address). Save
Configuring the firewall
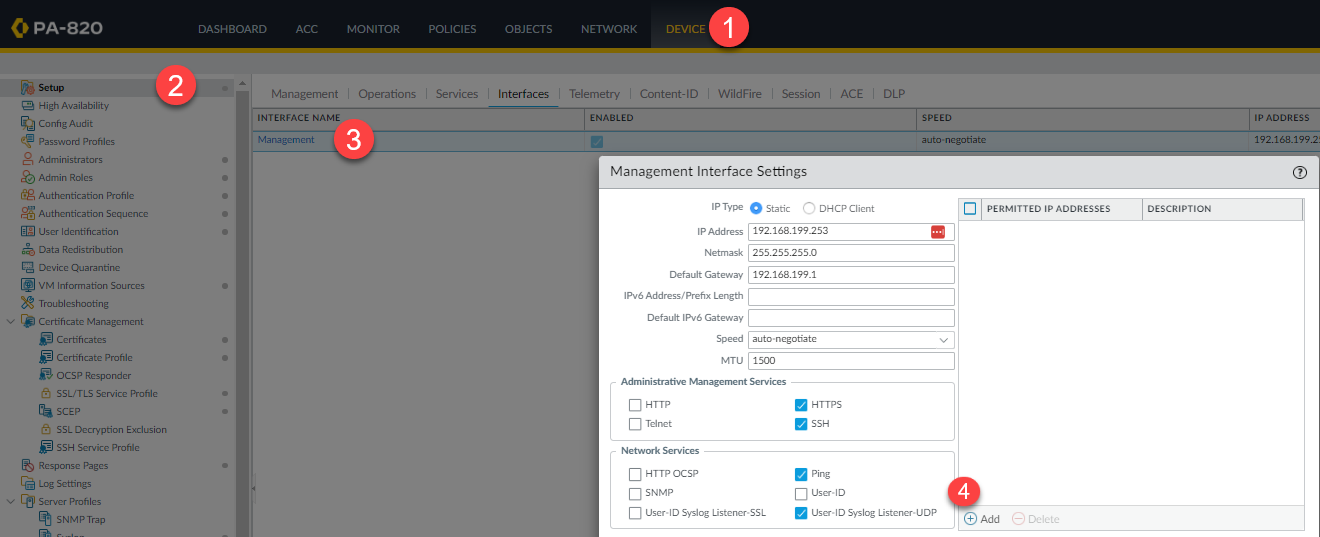
User-ID can be configured per zone (for data interfaces), or it can be configured on the management interface. Here, we are going to use the management (MGMT) interface to keep load off of the data plane. These steps configure the MGMT interface to accept incoming syslog messages. Again, you can use an alternative interface if you wish.
Navigate to Device -> Setup -> Interfaces -> Select the interface that you want to accept syslog messages. We are configuring User-ID with UDP 514 which is unencrypted.
Configure the firewall to parse the log files.
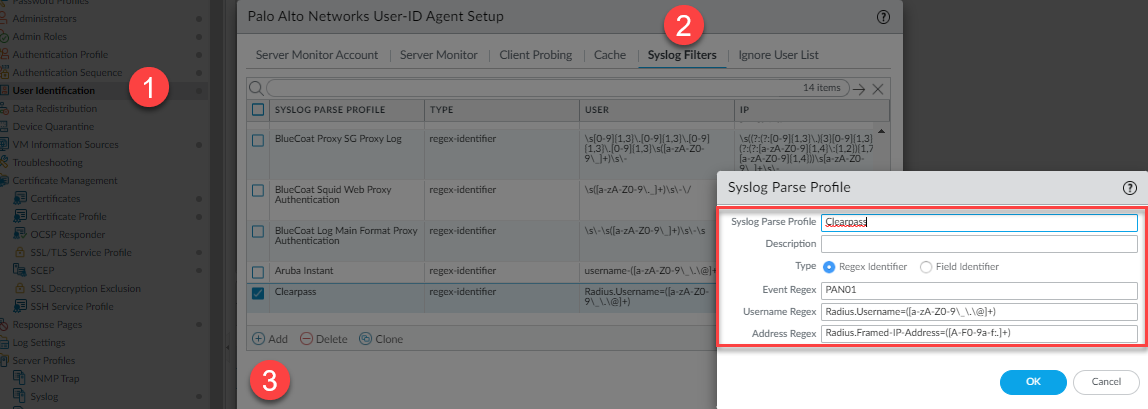
Navigate to Device -> User Identification -> User Mapping -> Gear Icon -> Syslog Filters <tab> -> Add
Syslog Parse Profile: Clearpass
Type: Regex
Event Regex: PAN01 <— from what you named the syslog target in CPPM.
Username Regex: Radius.Username=([a-zA-Z0-9\_\.\@]+)
* EDIT: If Windows machines are authenticating this regex will not catch it. However, you can modify it as such to catch those as well: ([a-zA-Z0-9\_\.\@\/]+)
Address Regex: Radius.Framed-IP-Address=([A-F0-9a-f:.]+)
Now we need to configure the device(s) we will accept the syslog messages from.
Navigate to Device -> User Identification -> User Mapping
Click the "Add" button under Server Monitoring.
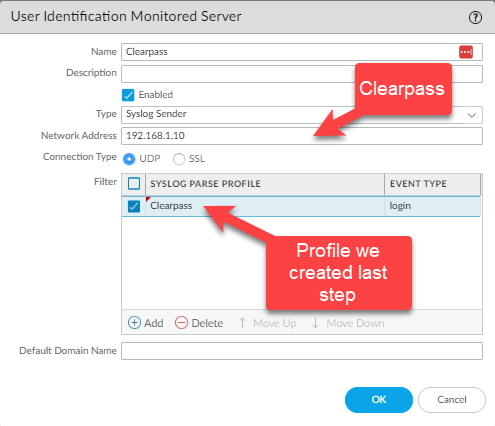
and that is it.
NOTES:
-
The User-ID that is submitted LAST wins with the PAN NGFW. Meaning, if syslog submits an USER-ID mapping, then Global Protect submits one, GP wins because it came second.
-
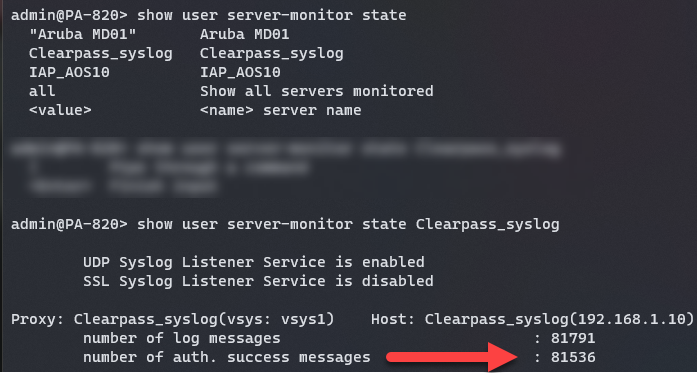
CPPM sends syslog message in batches. This means that the IP mappings will be delayed. I've seen 5 minutes and longer. So, I'm not quite sure what the schedule is.
-
Insight has to be enabled on CPPM server sending syslog messages for this particular solution.
-
Tested Versions:
- CPPM 6.10.8, 6.11.0, PAN NGFW 10.2.2
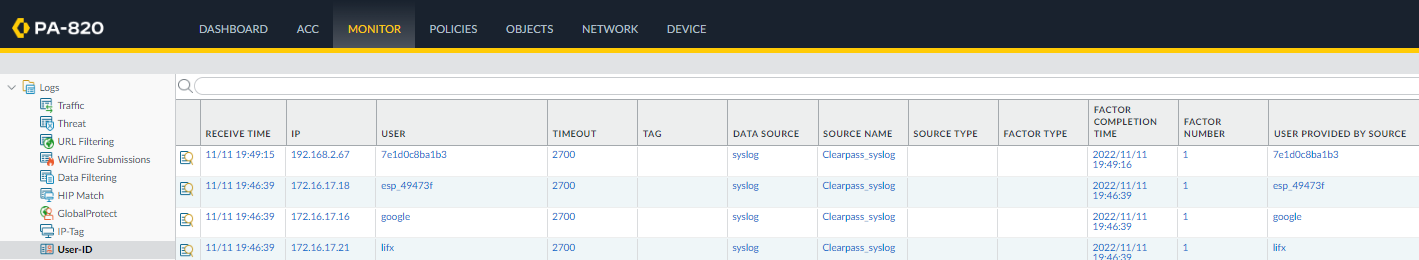
Verification: